Authentication 101
Basics
Authentication is the process of verifying who a user is.
Authorization is the process of verifying what users have access to.
A real-world example, when you go through security in a college, you show your ID to authenticate your identity that you are from that college. Then, when you enter your department or classroom, you present your department from the ID, so they can authorize you to get into the department and go only to your authorized class. You can't just sit in another department's class as you won't be authorized for the same.
To summarise, access to a resource is protected by both authentication and authorization. If you can't prove your identity, you won't be allowed into a resource. And even if you can prove your identity, if you are not authorized for that resource, you will still be denied access.
Authentication types:
Password-Based Authentication
Passwordless Authentication
OTP-based Authentication
2FA/MFA (Two-Factor Authentication / Multi-Factor Authentication) etc.
Authorization types:
Role-Based Access Controls (RBAC)
OAuth 2.0 Authorization (lets an app access resources hosted by other web apps on behalf of a user without ever sharing the user’s credentials. Eg: Fb, Twitter, Google login/signup)
JSON web token (JWT) Authorization
Common authentication and authorization types:
JWT-based:
In authentication, when the user successfully logs in using their credentials, a JSON Web Token will be returned. Since tokens are credentials, great care must be taken to prevent security issues. In general, you should not keep tokens longer than required.
Generate a JWT token in the backend that is specific to a user using a private key, pass this JWT token to the frontend, and then our frontend can send this token alongside requests to access protected API routes.
Whenever the user wants to access a protected route or resource, the user agent should send the JWT, typically in the Authorization header using the Bearer schema.
The server's protected routes will check for a valid JWT in the Authorization header, and if it's present, the user will be allowed to access protected resources.
Two-Factor Authentication:
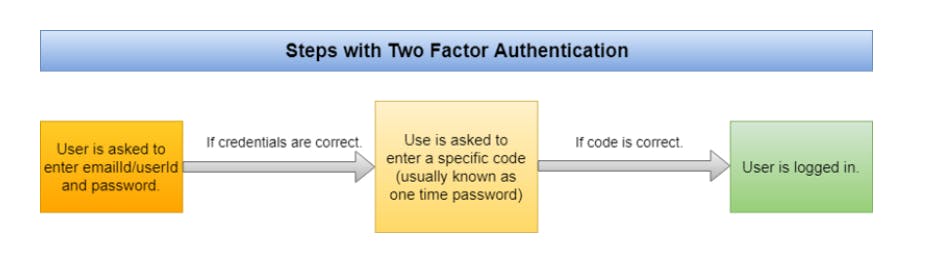
First we use password-based authentication and then we again verify the user by sending a one-time password.
Advantages of using OTP-based authentication:
Even if the OTP is stolen, it cannot be used again as it expires after a certain time limit.
Users generally tend to keep the same passwords on multiple websites, so even if one is hacked, all the other websites and services can be hacked. OTPs are dynamic, the codes are unique and become invalid within minutes, which prevents attackers from obtaining the secret codes and reusing them in other websites and solves the above-mentioned problem.
Robot Blocking: This system is also very useful in blocking robots that generate automatic profiles and perform persistence tests.
=================
